Responding to Cybersecurity Threats & Failures
In this section, we summarise key cybersecurity practices from both government and industry, primarily collected from the NIST Cybersecurity Framework1 and Google’s Infrastructure Security Design Overview paper2. These serve as an introduction to the steps that need to be taken to define and protect against threats, detect incidents when they occur, and respond to and recover from them.

Defining Threats
The first step towards defining threats is threat modelling. It is the process of enumerating potential risks to security in order to develop appropriate safeguards against them.3 In the context of digital ID systems, this entails:
Enumerating ‘Attack Surfaces’: Defining the various points of potential compromise, or the ‘attack surface’, of a system. This can include every entity that handles personal identity information or sensitive metadata, such as the various points of enrollment and authentication, central databases where such information is stored, and the network that carries information between these points.
Assessing Risk & Harms: Assessing the risk and harms associated with compromise implies adopting security measures that are proportionate to the harm that a data breach may cause. For instance, compromise of a large centralised database would have a larger impact than compromise of a single enrollment centre that serves a small number of individuals.
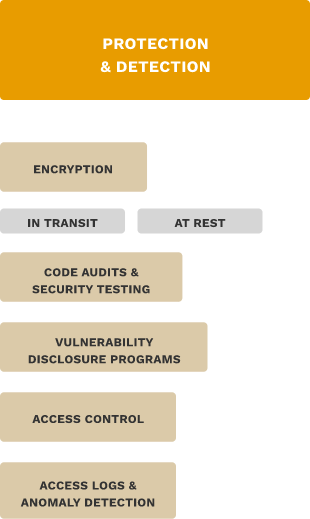
Protection & Detection
It is necessary to put in place mechanisms to protect against cyber attacks and detect incidents. The key considerations are:
Encryption in transit implies encryption of information while it travels from one point to another over a network. This includes private links between infrastructural entities as well as over public networks such as the Internet.
Encryption at rest refers to the encryption of data while it is stored. This protects data from attacks or flaws in the storage infrastructure, such as an untrusted storage device or unauthorised physical access to the storage disks.
Code audits and security testing is the implementation of both manual and automated processes to attempt to identify vulnerabilities before they are exploited by malicious actors.
Vulnerability disclosure programs provide safe harbour for security researchers to responsibly identify and disclose flaws in digital infrastructure.4 This reduces the potential for misuse by malicious actors.
Access control is the process of setting policies that ensure entities can only access data when they are authorised to do so.
Access logs and anomaly detection is the process of maintaining and monitoring records about what data was accessed, when, and by whom. In the context of digital ID systems, this information can be sensitive in nature, so access logs should be maintained in aggregate or de-identified forms.
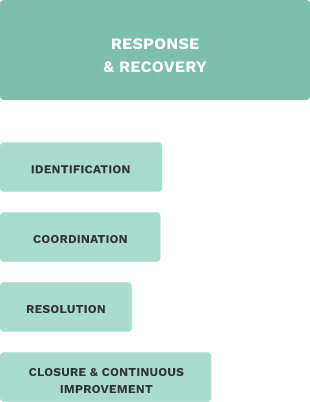
Response & Recovery5
Responding to a cybersecurity incident entails ascertaining what data is breached and what services are affected, removal of any ongoing unauthorised access, and restoring data and services impacted by the incident. Broadly, the steps involved in incident response are:
Identification: An incident can be identified either through the manual or automated processes put in place for detection beforehand, or by observation of the effects of the incident.
Coordination of the various operational and technical activities, such as triage, mitigation, and restoration of services. Resolution involves finding the root cause of the issue, limiting its impact, implementing identified fixes and restoring all data and services affected. An important aspect of resolution is notifying the individuals impacted by the breach. Closure and Continuous Improvement is the process of documenting and understanding failures, and putting in place processes to avoid future incidents.
Notes
| 1 | Matthew P. Barrett, Framework for improving critical infrastructure cybersecurity (National Institute of Standards and Technology, Gaithersburg, MD, USA, Tech. Rep, 2018). ↑ |
| 2 | “Google Infrastructure Security Design Overview”, Google Cloud, last accessed November 12, 2021. https://cloud.google.com/security/infrastructure/design. ↑ |
| 3 | Adam Shostack, Threat modeling: Designing for security (John Wiley & Sons, 2014). ↑ |
| 4 | Improving the Processes for Disclosing Security Vulnerabilities to Government Entities in India (January 23, 2019), https://cis-india.org/internet-governance/resources/Improving%20the%20Processes%20for%20Disclosing%20Security%20Vulnerabilities%20to%20Government%20Entities%20in%20India.pdf. ↑ |
| 5 | “Data incident response process”, Google Cloud, last accessed November 12, 2021. https://cloud.google.com/security/incident-response. ↑ |
